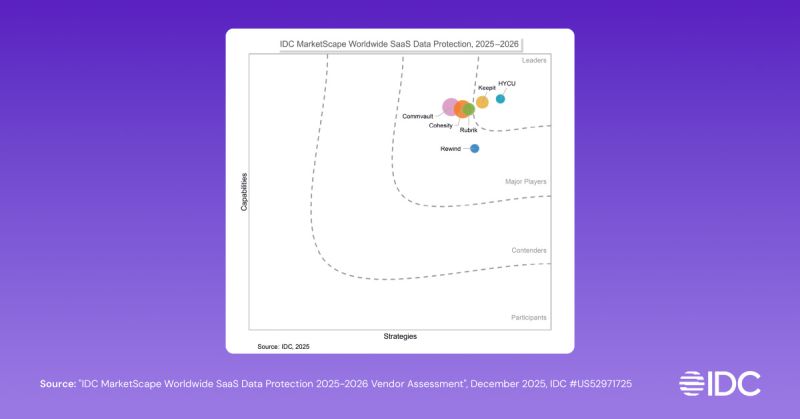
HYCU Unveils R-Shield™, Data Resiliency for R-Cloud Customers
The Stakes Have Shifted. Data Protection Must Catch Up.
For years, ransomware was the primary threat. Immutable backups and air-gapped copies helped bring businesses back from the brink, and in many cases, made paying a ransom unnecessary. But attackers adapted.
Now, they’re expanding into new areas: fragmented infrastructure and unprotected SaaS apps.
Here’s where the cracks are showing:
- Legacy protection can’t keep up. Most solutions were built for legacy infrastructure and generic servers, not for intelligent virtual or cloud environments. Retrofitting isn’t a strategy, it’s a risk.
- The SaaS estate is exposed. Enterprises rely on hundreds of SaaS apps, but most vendors protect just a handful. Git repos, cloud drives, knowledge bases are business-critical tools that remain vulnerable to error, abuse, and attack.
It’s no longer enough to protect what’s familiar or easy. The new standard is this: protect everything that matters with no blind spots, no compromises.
HYCU Introduces Resiliency Shield to Offer Customers Total Coverage for SaaS, Cloud, and On-Premises
At HYCU, we set out on a mission to protect the entire data estate. With the introduction of HYCU Data Resiliency Cloud (R-Cloud)™ two years ago, we provided thousands of customers the ability to protect their entire data estate with 80+ workloads and counting. Data protection for the entire data estate is critical, but with recovery as a last line of defense, customers need the ability to protect and recover workloads across any threat on any application.
That’s why we’re excited to introduce R-Shield™ - a cyber-resilience fabric built-in to the HYCU R-Cloud platform, designed to help customers gain resilience, no matter the workload, no matter the threat. This cyber resilience fabric allows customers to stay:
- Always Protected. Starts with a backup infrastructure that is securely built with military grade technology that also ensures your data is always hidden from your enemies. Protect all your critical workloads (not just a few) with your data always under your control with customer-owned, immutable backups.
- Always Observing. Complete visibility of their entire data estate to expose risk, and deep anomaly detection and ransomware-scanning at the application layer for rapid response.
- Always Ready. Inspite of all the protection and prevention, customers need to be always ready to recover what they need when they need. Customers can rest assured knowing they have validated backups and can recover any workload or specific data with confidence and according to their runbooks. Whether insider threats, supply chain attacks, ransomware attacks, or simple human error – customers will have access to their data when they need it to where they need it.
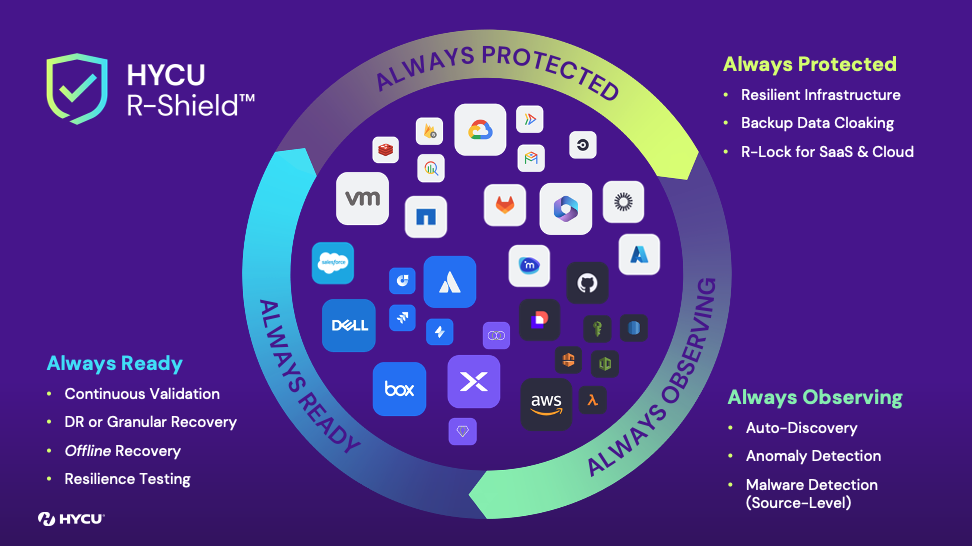
Always Protected
Reduce the Attack Surface: Backup Data Cloaking & Resilient Infrastructure
Backups are now a primary target for attackers. According to Sophos State of Ransomware Report 2024, 94% of organizations hit by ransomware in the past year said that the cybercriminals attempted to compromise their backups during the attack. It’s critical that your backups are not easy to find, and that your backup solution is secure, hardened and battle tested.
HYCU reduces your backup attack surface in three ways:
- Hardened and military grade. Starts with the right architectural principles. HYCU secures your backups with a hardened virtual appliance trusted by federal agencies. With military-grade architecture and certifications like DISA STIG, Common Criteria, and vTPM, your data stays isolated, protected, and ready—no matter how sophisticated the attack.
- Agentless Architecture. Complexity of infrastructure is one of the biggest enemies to keeping data safe. HYCU eliminates backup complexity, and risk, with a zero-design architecture that eliminates agents or multitude of standalone servers and leverages native APIs with no backdoors.
- Backup Data Cloaking: There is no need for the backup data to be visible to anyone other than the backup service. By providing the option to isolating backup traffic in a secure, independent network, HYCU creates a barrier between the production networks and the backup data. In addition, HYCU realizes that environments are dynamic and there are times where customers cannot keep isolated networks, so it provides continuous monitoring of who has access to the backup data and warns the customers when non-HYCU participants have access to the data to take immediate action.
R-Lock™ - Immutable, Offsite Copies
All mature organizations have immutable, offsite copies for their on-premises workloads. Following the 3-2-1 rule is a decades long approach. However, when it comes to SaaS applications, customers face two issues:
- Limited coverage. Most vendors protect Microsoft 365, Salesforce, and little else—leaving critical tools like GitHub, Box, and Confluence exposed.
- Vendor-controlled backups. Customers often relinquish control, increasing third-party risk.
With R-Lock, HYCU is the only solution that delivers enterprise-grade immutability across 80+ SaaS and cloud workloads. No vendor lock-in, just storage efficient, immutable backups stored in your cloud or on-prem storage. You own the data, the destination, and the recovery path. That’s true resilience, at scale.
Let’s use apps like Jira & Box. Customers can store copies with rapid, object-level immutability at any frequency they desire. If a disgruntled employee begins deleting critical files, HYCU users can simply select a safe point in time and restore these files from a secure, immutable copy that is stored efficiently.
Always Observing
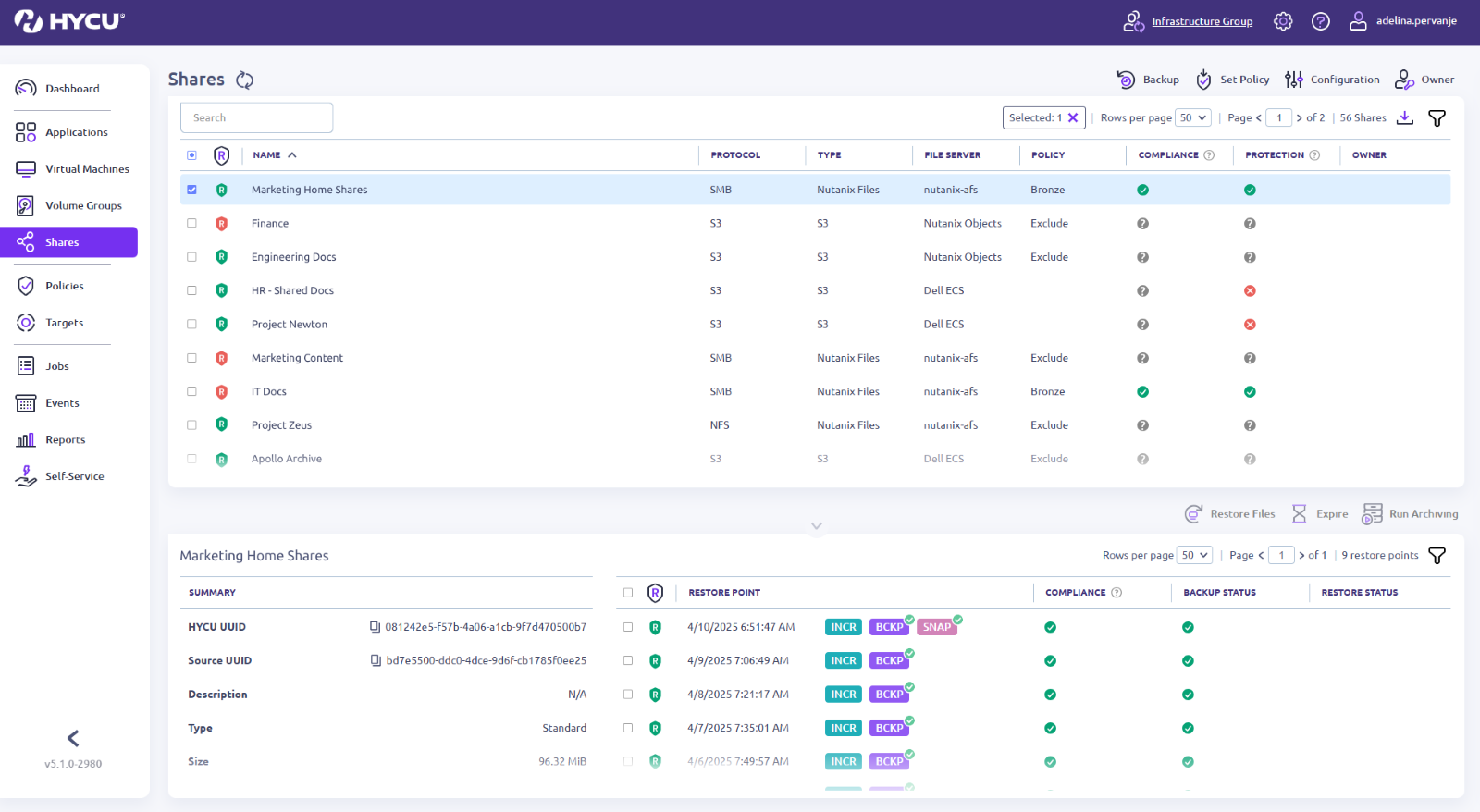
Visualize Protection Status of your Complete Data Estate
In a traditional data center environment, customers had complete control and visibility of all of the services that were deployed. In the world of Public Cloud and SaaS, it’s easy for IT teams to lose track of what and where services and applications are being used. Often, workloads like AWS IAM, Lambda, GitHub and DocuSign carry immense value and are often unprotected and overlooked.
With HYCU R-Graph, customers can automatically discover and instantly visualize their entire data estate and expose the services and application every single department is using. Then, teams can immediately view and understand which applications don’t have any validated recovery, backups, or data retention capabilities. This helps expose cyber and compliance risk – in one single map.
Continuous Data Smart Anomaly Detection
A big part of observing for anomalies is not just detection, it’s about how fast can we detect them. There are a variety of heuristics employed in the industry. One of the most used and well understood method is the amount of data change. While it might sound this is just as simple as running an Excel function to look at the standard deviation over a period of time, to do it right and to eliminate too many false alerts, smarts must be built into the system. HYCU has this built in for the traditional workloads like VMs and Filesystem by tracking the change range between backups.
While data change rate is good for traditional workloads running in VMs, Apps and Filesystem, SaaS is a different beast. Standard capacity change is not the right way. Imagine, adding new users in an Identity management system like Okta might sound simple, the capacity that it adds is miniscule to the total, so the standard “data change rate” will not capture it. We need to track the object level updates. HYCU tracks things like number of add and deletes to Okta and that allows customers to see if there are anomalous activities going on in the critical infrastructure.
Source-Level Malware Detection
Early threat detection is essential to minimizing disruption—but most backup tools come with tradeoffs. Traditional approach by vendors have been one of two approaches:
- Mount the backup onto a new server and run the checks
- Rely on scanning metadata hours after backups complete, often in their own SaaS control planes.
In both cases, due to complexity of data movement, only a select set of data is scanned. This creates a false sense of security and/or creates a delayed detection. In the external cloud meta data shipment, it also introduces a new attack vector: your vendor. With sensitive data effectively handed over and scanned outside your environment, dwell times remain high, and the risk surface expands.
HYCU takes a fundamentally different approach. We scan real data—right at the source—before it ever leaves your environment. That means faster, continuous detection without compromising performance or control. There’s no vendor data access, no delayed uploads, and no centralized scanning that puts your data at risk. With support for any backup target, HYCU gives you tighter control and a dramatically reduced blast radius. Data stays where it belongs: in your hands.
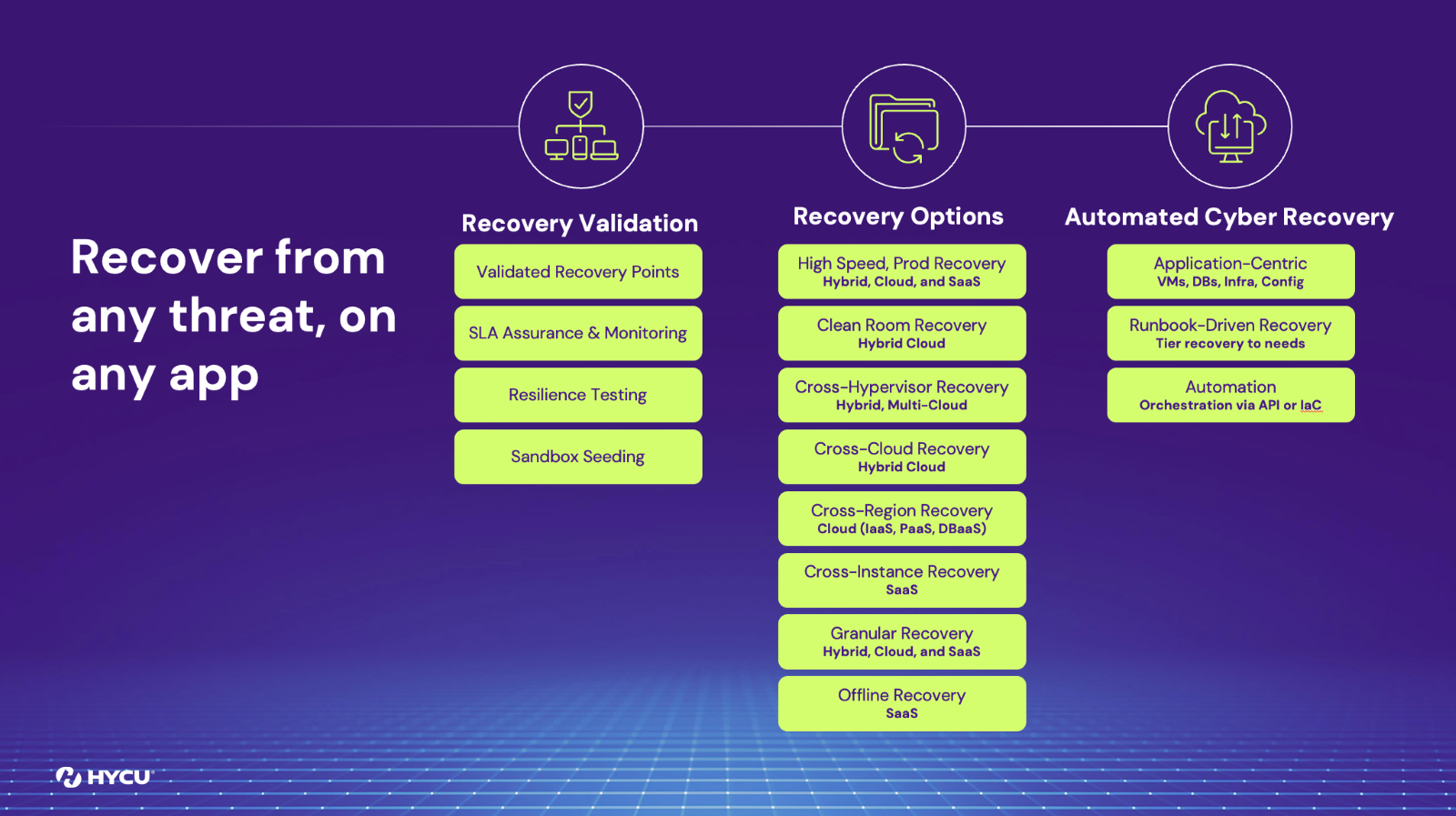
Always Ready
Validated Backups: Recover with Confidence
As the saying goes, “practice makes it perfect”. Recovery is no different. Customers should always continuously validate that the system and the infrastructure is always ready for recovery. HYCU makes it easy for customers to set up continuous validation. Traditional validation is just bringing up a VM, sending a ping, and marking it ‘good’. While that’s a start, it’s not enough. HYCU goes further by validating databases and applications themselves, giving teams true confidence that everything critical will function when restored.
Flexible Recovery Options
Every recovery scenario is different. Some situations call for surgical restores. Others demand full application recovery to alternate systems, instances, hypervisors, or even across clouds. That’s why HYCU offers a wide range of recovery options. Options so customers can choose what works best for them. Whether you need to recover a specific file or move an entire environment to another platform, HYCU ensures you get your data back, when and where you need it.
Automated Cyber Recovery
When it’s time to recover, customers may need more than just individual workloads—they may need entire applications brought back online, including VMs, file systems, databases, and object storage. HYCU automates this full-stack recovery process to make restoration fast and efficient. For even more control, HYCU supports orchestration through Intentful REST APIs and tools like Terraform Provider. Whether recovering locally, to a different cloud, or across infrastructures, automation ensures a smooth, coordinated return to service.
Offline Recovery from Supply Chain Attacks
Cyber attackers have turned their focus to high-value SaaS and cloud providers, where a single breach can compromise thousands of customers. From LastPass to Typeform to Snowflake, the pattern is clear: no provider is immune. That’s why resilience can’t stop at backups, it must include a plan for regaining access to critical data when the service itself becomes unavailable. When vendor systems are breached or go offline, your teams can’t afford to wait hours or days for access to vital information.
With HYCU R-Shield, customers gain a powerful safety net: offline recovery. This capability provides readable access to SaaS data—independent of the app or provider. Already live for platforms like Jira and Box, offline recovery ensures that even if your SaaS vendor is compromised, your data remains accessible when you need it most. HYCU continues to extend this feature across more workloads, so customers stay in control, even in the face of the unexpected.
Conclusion
While threats have changed, so should your resilience strategy to keep up and minimize those threats.
R-Shield is a layer of protection. But it’s not just that. It’s a built-in resilience fabric that empowers your team to see more, recover faster, and stay in control across your entire data estate. From immutable backups to offline recovery, from deep observability to automated restoration, R-Shield makes sure you’re always protected, always observing, and always ready.
Join us on Tuesday, April 29th at 10:00 a.m. ET/4:00 p.m. CET for an unveiling webinar, “Full Stack Cyber Resilience for SaaS, Cloud and On-prem." If you can’t make it, a replay will be available.
Or, you can see it in action and request a demo of R-Shield today.
Get the newest insights and updates
By submitting, I agree to the HYCU Subscription Agreement , Terms of Usage , and Privacy Policy .