Image
Total Cyber Resilience for Your Entire Data Estate
Protect your entire data estate with HYCU R-Shield™, the proactive solution designed to detect, prevent, and recover from ransomware, insider threats, and supply-chain attacks—keeping your data secure, accessible, and fully under your control.
How it works
HYCU R-Shield: Built-In Cyber Resilience for SaaS, Cloud, and On-Prem
Image
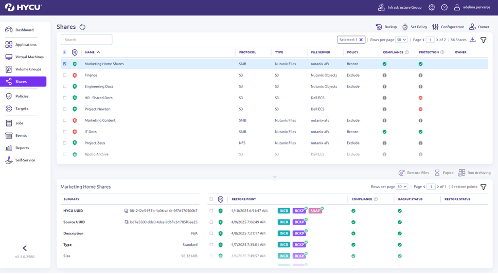
Reduce your Backup Attack Surface
Attackers target backups. HYCU keeps yours hidden and ready to recover.
- Hardened backup service: Built on a military-grade virtual appliance with DISA-STIG certification.
- Agentless by design: Native APIs and no proxies mean less complexity—and fewer entry points.
- Backup data cloaking: Continuous Backup Target Security Posture Management and Isolates backup traffic in a secure, invisible network—undetectable to attackers.
Image
Real-Time Threat Detection – No Trade Offs
Catch ransomware early, without sacrificing privacy or control. Detect ransomware early—before the damage spreads.
- Scans at the source: Analyzes live data—not just metadata—for faster, earlier detection.
- Zero vendor access: No uploads, no data exposure, no compliance friction.
- Empowers SecOps: Get timely, actionable alerts—without legal or operational delays.
Image
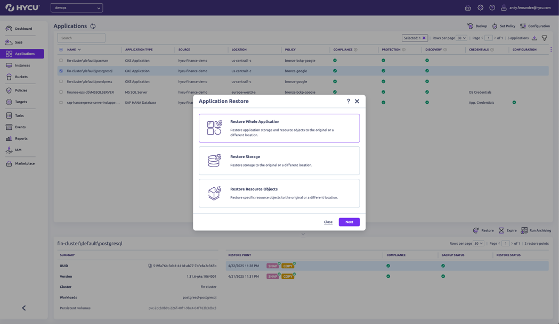
Fast, Flexible Cyber Recovery on Your Terms
Whether you’re facing ransomware, user error, or a full outage:
- Orchestrate recovery across SaaS, cloud, and on-prem—without agents or vendor bottlenecks.
- Use runbook-defined workflows and infrastructure-as-code to automate critical restores.
- Recover in minutes, not hours. Speed reduces pressure, limits ransom leverage, and keeps your business moving.
Image
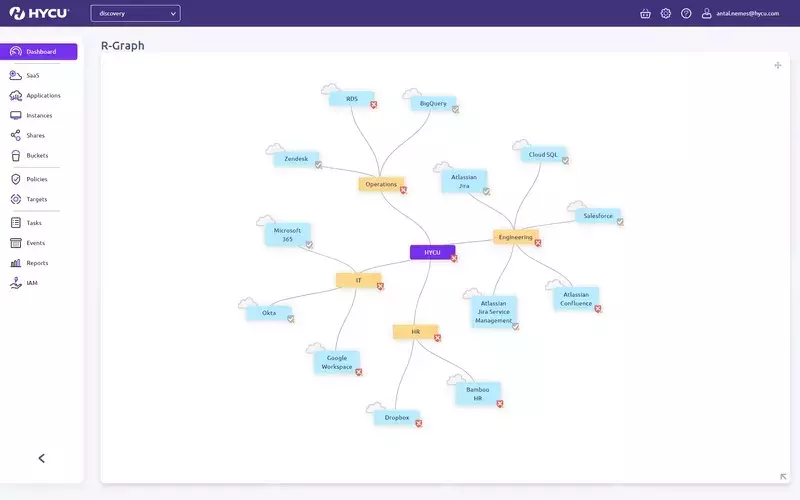
Third-Party Visibility Beyond IT
See every SaaS app. Know what’s protected.
- Map by department: Visualize usage and ownership to prioritize
- Uncover risk: Automatically discover third-party apps across your organization
- Expose coverage gaps: Identify apps without backup, recovery, or offsite protection
Image
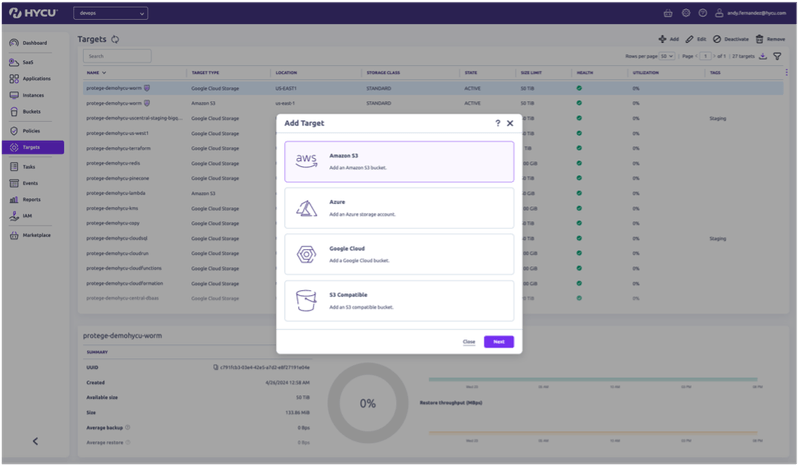
Immutable, Offsite Copies with R-Lock™
Lock down backups across all applications, including SaaS
- Backup destination control. You choose where your data lives—your cloud, your storage, your rules.
- Verified, unchangeable backups—without vendor lock-in or hidden exposure.
- Protection without compromise. No scripts. No shortcuts. Just clean, immutable copies that restore when it counts.
Image
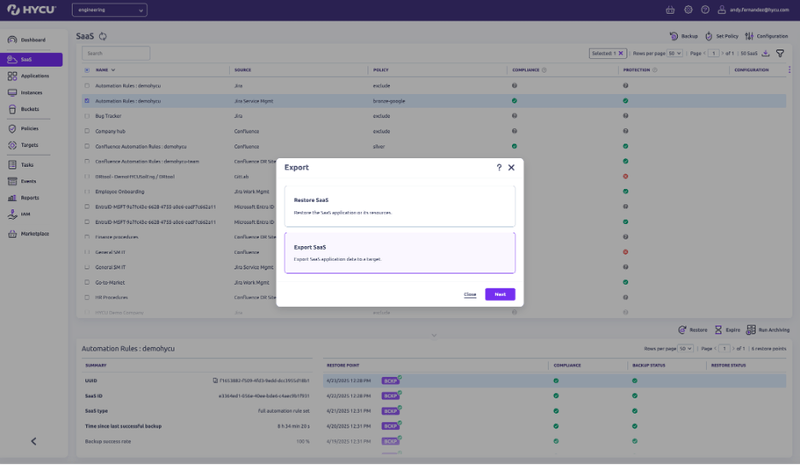
Built-In Supply Chain Resilience
If your SaaS goes down, your business won’t.
- Independent recovery: Store backups outside the provider’s environment—stay in control.
- Continuous access: Access critical data even if GitHub, Box, or your CRM is compromised.
- Compliance-ready: Meet SLAs and regulatory requirements—even during major outages.
Additional Resources
HYCU R-Shield: Insights and Solutions
Demo
It’s time to protect your entire data estate, not just a fraction
Image
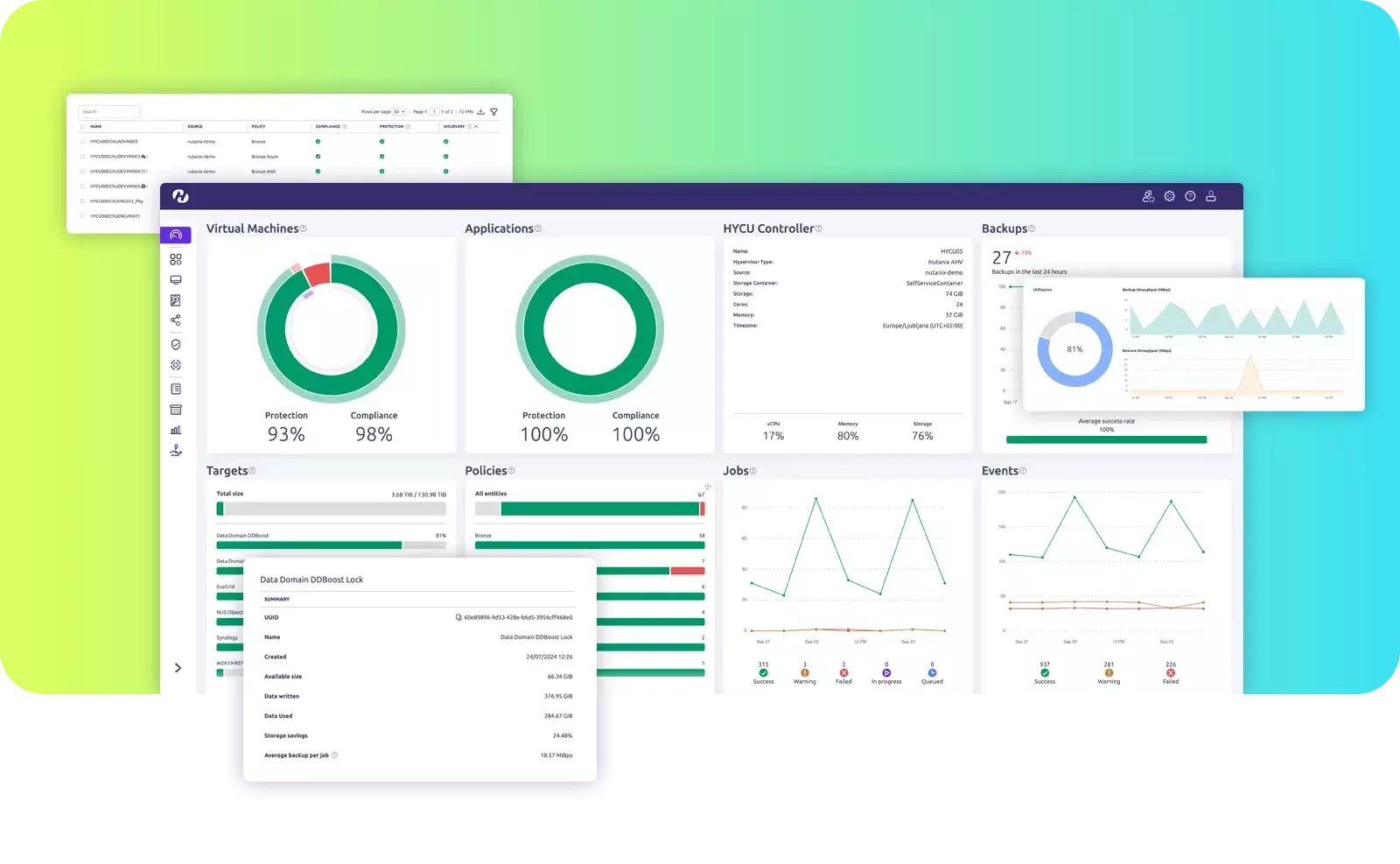
The only solution with comprehensive data protection
- See how R-Shield™ detects and protects hybrid, multi-cloud, and SaaS environments.
- Real-time anomaly detection and malware scanning at the source.
- Discover instant visibility into as-a-service applications and their protection status.
- Learn how R-Lock™ secures your critical data with offsite, tamper-proof backups.
- Experience the intuitive interface designed for simplicity and control.
Request a demo
We look forward to assisting you in your journey to see why so many organizations choose HYCU.