A few day ago, I had a great conversation with an ASM specialist around how ASM can be included in DevOps.
Every application developed and deployed needs robust protection, and using ASM as an application firewall offers an excellent solution. The strength of ASM lies largely in its policy-based approach, which allows for precise control through the description of allowed and blocked signatures.
Developers, being the architects of their applications, possess an unparalleled understanding of their creations. This intimate knowledge makes them ideally suited to develop ASM security policies tailored to their applications' specific needs and vulnerabilities. By empowering developers to craft these policies, organizations can create more effective and efficient security measures that align closely with the application's architecture and functionality.
However, policy development is only the first step. Rigorous testing is crucial to ensure the effectiveness of these security measures. This is where centralized tools like our SCOM F5 BIG-IP Management Pack prove invaluable. This comprehensive solution provides detailed reports on all blocked sessions, offering crucial information such as:
- When the session was blocked
- Why it was blocked
- Which specific policy triggered the block
These reports serve a dual purpose. They can be used for manual review, allowing developers and security teams to analyze the effectiveness of their policies and identify any potential issues. Additionally, the ability to export these reports to CSV format supports automated testing processes, seamlessly integrating security testing into continuous integration and deployment pipelines.
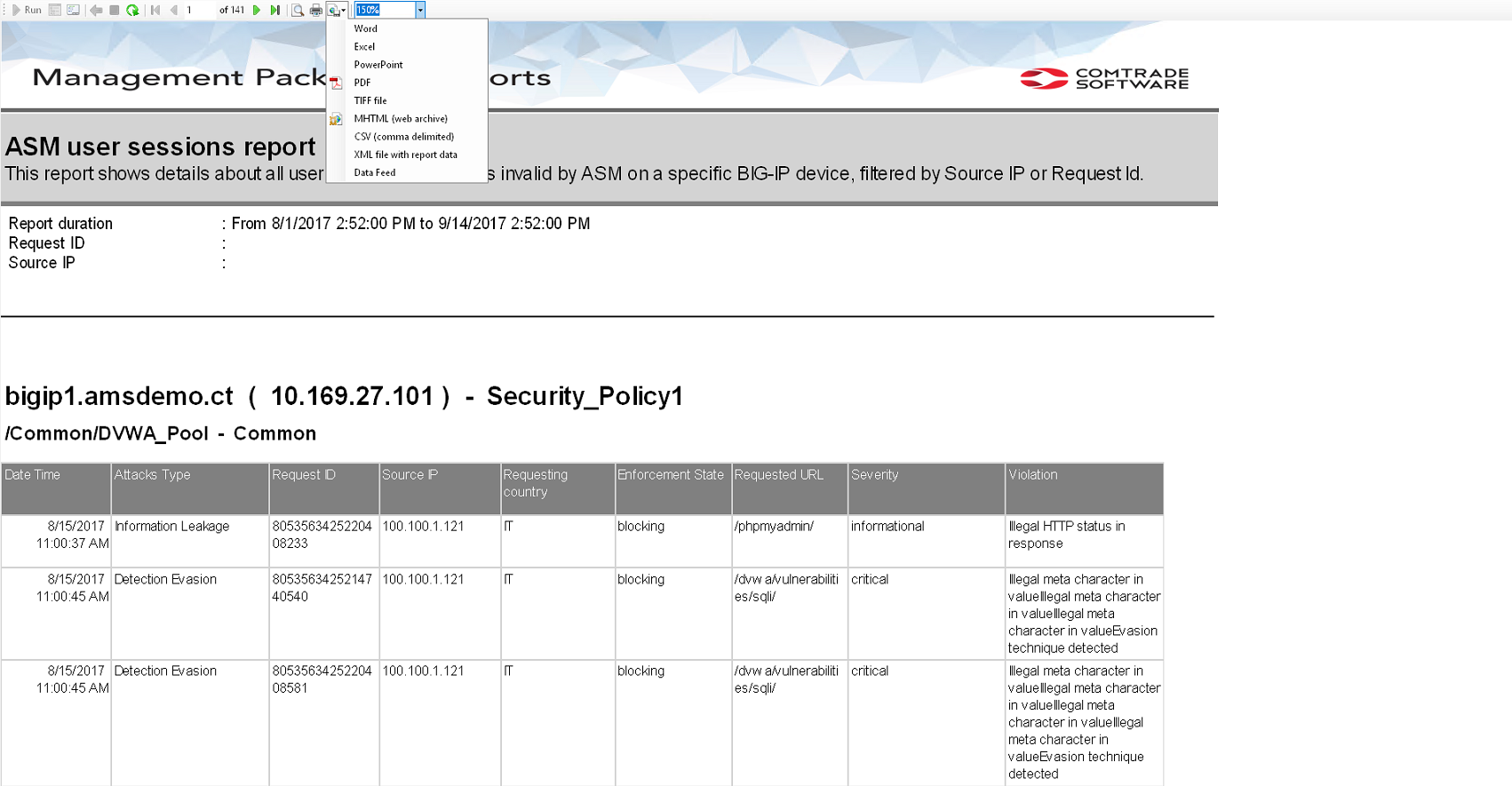
Report showing list of blocked sessions, when, why and by which policy the session was blocked
This report can be used for manual review of results or exported automatically to CSV to support automatic tests.
Once developers are happy with the policy they can send it for “peer review” by ASM specialists.
One item ASM specialists may appreciate is that they can use our SCOM F5 BIG-IP Management Pack as a communication tool to report any blocked solutions. By using SCOM this report can be automatically attached to an issue tracking system issue or delivered i.e. by email.
Once approved by ASM SME, developers can script policy deployment with a new application version deployment.
If you're exploring ways to integrate and test ASM within your DevOps pipeline, we encourage you to take a closer look at our solution. It offers a comprehensive approach to application security that aligns with modern development practices.
To experience these benefits firsthand and see how our solution can enhance your application security strategy, we invite you to try a free evaluation. This hands-on experience will demonstrate how our SCOM F5 BIG-IP Management Pack can streamline your security processes and foster better collaboration between your development and security teams.
Get the newest insights and updates
By submitting, I agree to the HYCU Subscription Agreement , Terms of Usage , and Privacy Policy .
