How to Create a Future-Proof Data Protection Strategy
Are you worried about the security of your own data?
You should be. As you know, data privacy and data protection are hot topics in the media. This is due in part to high-profile data breaches, Facebook’s careless handling of its users’ personal data, and large-scale initiatives like the General Data Protection Regulation (GDPR) legislation, which goes into effect on May 25, 2018 in the EU.
It’s clearly top of mind for everyone, businesses and individuals alike.
As I look back, traditional data protection was incredibly complex for businesses, both small and large. Concerns for which data to back up, how long the data needed to be kept and compliance issues including adhering to the rules found in the Data Protection Act 1998 (which safeguards the right to privacy when organizations or businesses process your personal information), the Financial Services Act 1986, and the Freedom of Information Act have always been front and center.
Now as we think about newer initiatives like the General Data Protection Regulation (GDPR), organizations are looking at ways to be compliant or they risk heavy fines. For example, with GDPR, professional services firms as data controllers will face “effective, proportionate and dissuasive” administrative fines of up to 4% of their annual global turnover or €20 million – whichever is greater – for data breaches. Sadly, (according to IDC’s 2018 Western European Partner Survey), nearly half of European Channel Partners surveyed say they are still figuring out GDPR and what it means for their business. In other words, one month to go and they are not ready. One month to go and many are not compliant. One month to go and the countdown to heavy fines begins.
Why GDPR Matters to All of Us
It’s easy to assume that GDPR is not relevant to your business because it happens to be located elsewhere in the world. But the fact is, if you are participating in this global economy at any level, GDPR will have an impact on your business. Futurists and savvy IT managers understand that the GDPR, and other large-scale data security initiatives that will most certainly follow, could potentially damage their organization either through the penalties of noncompliance or the cost of reputation from a data breach.
In other words, investing in a stronger, simpler data protection strategy for your essential business information is a no-brainer. And chances are while you are already looking to modernize your data center operations with the latest hyper-converged infrastructure offering from Nutanix, there’s never been a better time to couple that movement with the right data protection software solution to complement those efforts..
Common HCI Data Protection Mistakes
Sadly, today, much like organizations that may still only just be thinking about GDPR now, most organizations have designed their data protection infrastructure based on concepts from the 3-tier architecture era and run on a foundation of traditional backup and recovery software. Hyper-converged infrastructure (HCI) is one of the most noteworthy technologies to affect data protection of primary and secondary data storage systems. On the surface, it seems simple. Buy an offering, plug it into the data center and spin up the desired virtual machines (VMs). If more compute or storage is needed, simply add another box to the mix. Using the capabilities of the ‘out-of-the-box’ data protection from the HCI platform may work in some cases, but often does not provide a complete protection strategy.
You want your data protection to run the same way as your HCI infrastructure.
In order to do that you need
- Data protection that breaks down silos
- Simplifies protection strategies
- Understands Applications in an impact-free way
- And is fully integrated in the overall solution
Some of the most common mistakes that we’ve observed in our customers’ data storage infrastructure are around data protection for HCI include the following:
- Treating HCI like traditional infrastructure - ignoring the intelligence and not leveraging the already available extremely efficient snapshots, clones, replications, deduplication and compression
- Acting like virtual machines are black boxes - not understanding the applications running in the virtual machines, or not addressing the "VM stun” or the quiescing of the VM for a snapshot
- Carrying over legacy complexity - when consolidating resources utilizing HCI, using legacy, complex data protection does not allow the HCI deployment to reach its full potential
These are just a few examples of common HCI data protection mistakes that we’ll be exploring together, so stay tuned for upcoming posts around this topic. But in today’s changing environment, you need to be ready to address several new challenges for an effective data protection strategy.
New Data Compliance Challenges
So, what does this all mean? The rules are changing--and will continue to evolve as large-scale information security regulations, like GDPR, are issued. This means you need a data protection strategy that is simple, effective, and lets you embrace a flexible approach as needed to completely redo your approach, without having to make surprise investments.
The Evolution of Data Compliance
With GDPR, we see additional rules being put in motion from the European Union, but clearly, the role of compliance will continue to grow globally. So, it makes sense to consider an approach that allows a global adoption of protecting data sets.
For example, GDPR limits data collection to only that which is necessary for a particular purpose. This focuses the protection of data retention on retaining and using what is required, nothing more. This is a fundamental shift in how businesses traditionally manage data. When “thinning” the level of data protection, businesses will be required to review their data collection practices and remove data that does not apply. This type of regulation will impact global business lines, so it needs to be built into your data protection best practices.
Here are some other factors to consider when creating and deploying your modern data protection strategy so you best align with emerging requirements:
- Rights to Information - As we learned from the recent challenges with Facebook, users embraced this recalibration of social relations without thinking about who or what was behind them. A recent article, Zuckerberg, Facing Facebook’s Worst Crisis Yet, Pledges Better Privacy, acknowledged that third-party applications obtained access to “large amounts of personal information” from the social network.
- Data Governance - Proactively understanding what data is collected and why, who will have access as well as proactively apply the proper security measures to protect the access of data sets is key for data protection.
- Data Sovereignty - Protection of data across organizational boundaries is a daunting task. Global organizations are under the pressure to comply with regulatory and privacy requirements that vary from country to country. Data volume, variety, and complexity require organizations to manage data protection in different ways.
- U.S. Federal adoption - In the article “Nutanix Sees 74 Percent AHV Hypervisor Adoption By U.S. Federal Government Customers in 2017”, and also future supported by a recent article, ”Inflection Point in U.S. Federal Government Cloud Adoption” from Gartner, the growth in using a purpose-built data protection aligns and validates the Nutanix research, showing that the majority of federal government CIOs are poised to make a bigger push to the commercial cloud. This rapid adoption of cloud as well as Nutanix in the public sector combined with ongoing, evolving global regulations will require new solutions that can address these compliance challenges.
Go for Simplicity in Data Protection
As technology continues its unending evolution, so will the rules and regulations around data compliance. Meeting this challenge every day, every month, every quarter, every year will be standard operating procedure. The days of using complex, complicated methods to manage data are over.
That’s why we designed HYCU for Nutanix the way we did.
If you are looking to strengthen your existing data protection to drill down to the application level on your virtual machines running on Nutanix Acropolis (AHV) or VMware ESX, you have found it with HYCU for Nutanix. It lets you easily augment your foundational data protection with the full-featured, Application-Awareness technology to see through virtual machines running on Nutanix Acropolis (AHV) or VMware ESX hypervisors to detect the applications.
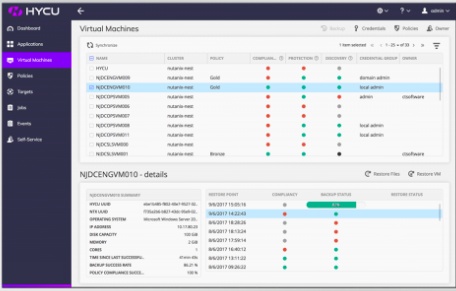
Virtual Machines View
We allow you to leverage Nutanix’s intelligent snapshots for rapid recovery and storage dense nodes for storing backups. Let employees use the hypervisors you have and the skills they know to manage robust data protection. And watch your CapEx and OpEx go down as your ROI soars. And we are talking about significant savings as one of our recent customers shared.
Share Your Data Protection Strategy
Does your system run on Nutanix? If so, do you agree? What are you currently doing to maintain robust data protection? If you’re like many IT leaders, you have a nagging suspicion that the data residing in your HCI is not as protected as it should be. Reach out to me to discuss how today’s challenges of data protection can be addressed and overcome with a purpose-built, focused approach to securing your information.
Learn More
Check out how to Protect Nutanix with HYCU data protection webinar to see how it works.
Get the newest insights and updates
By submitting, I agree to the HYCU Subscription Agreement , Terms of Usage , and Privacy Policy .
