Configuring F5 BIG-IP for the use of remote authentication is pretty straight forward and a common scenario
In order to give a remotely authenticated user access to the iControl REST API, user also needs to be added to the F5 device, using the procedure similar to adding a local account. To create this account, we should login to the BIG-IP Web UI and navigate to System >> Users >> User List and click Create. You will notice that the BIG-IP device asks only for the user name and the user role, it does not ask for the account password. This is because we are not creating a local account, but only specifying a role for the account that will receive iControl REST API access. This user will still be authenticated against the remote authentication provider.
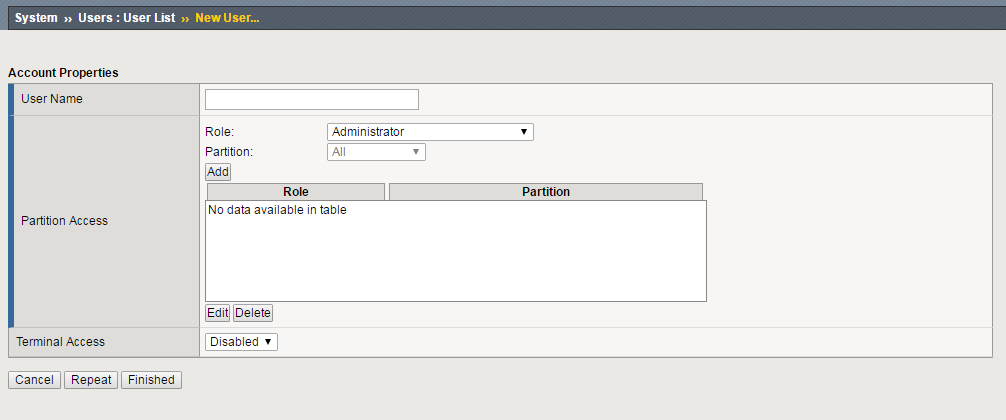
It is important to note that in versions 11.5.x of the BIG-IP device, it is necessary that the user has Administrator role. F5 introduced a role based access control with version 11.6.0 and above, where user can have also a guest role. We will cover this more thoroughly in the next section. If you are using remote role groups to define permissions for specific group of accounts, the accounts with Administrator level access will still not have access to the iControl REST API. The account that will be used to access iControl REST API must not be a member of any remote role group used on the BIG-IP device. In order to grant access to the iControl REST API, the user must be removed from these groups on the remote authentication provider. To check if the account that you wish to use has enough rights to access the iControl REST API, try accessing one of the endpoints and entering the credentials for the account that we have just configured. For example, you can try to access the following endpoint https:///mgmt/tm/cm/device?$select=version,managementIp.The BIG-IP device will prompt you for credentials and you should enter the credentials of the remote authentication account that was just configured. If the output is similar to this one:

then the account has been successfully configured. If the BIG-IP prompts you for credentials again then the account was not configured properly.
Using role based access control (RBAC) with F5 BIG-IP iControl REST API
With BIG-IP version 11.6.0, F5 has introduced the role based access control. In version 11.5.x, it was required that the user must have administrator rights, in order to access iControl REST API. These steps are really well documented in The user guide for the iControl REST interface in section “About iControl and RBAC for user accounts”. While developing Comtrade SCOM Management Pack for F5 BIG-IP, we have identified iControl REST API as a great interface with abundance of data that can be obtained through it. In conversation with the F5, we have come to the conclusion that iControl REST API is the F5 BIG-IP interface that they will continue to develop and improve. By resolving the issues mentioned above, we enabled our users to monitor their F5 BIG-IP devices and solve any issues before they significantly impact their system.
Additional Resources
Get the newest insights and updates
By submitting, I agree to the HYCU Subscription Agreement , Terms of Usage , and Privacy Policy .
